By: Bryan
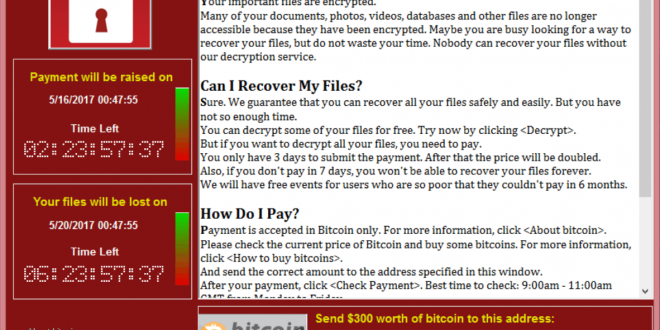
Recently, a ransomware called WannaCry spread across the world, locking computers and sealing their data unless 300 dollars in Bitcoin was sent to the captors. WannaCry finds and encrypts data files, then displays the ransom note. It spreads itself automatically by scanning for vulnerable systems, then exploiting the Windows OS to gain access. This attack has already spread to 150 countries and to more than 230,000 computers. Many major companies have been hit, such as Telefonica, FedEx, and Deutsche Bahn. The attack targets older versions of windows, such as Windows XP. Updated versions of Windows have security updates and are safe from the ransomware. A temporary kill switch was found by a 22 year old named Marcus Hutchins, but it has only slowed down the ransomware. After the initial outbreak and the discovery of the kill switch, a new version has been found that no longer has the kill switch.
So how is this ransomware able to do so much damage? Where did it come from, and how was it made? WannaCry uses EternalBlue, an exploit from Windows’s protocol. It was discovered by the NSA, but instead of reporting it to Microsoft, they kept it secret to do their own secret “work” (aka stalking). Microsoft released several emergency updates for older versions of windows, but the most affected OS was Windows 7. Most people at this point have updated their Windows version, and the spread of WannaCry has slowed considerably.
 Tempus Magazine By Students, For Students
Tempus Magazine By Students, For Students